This article explores how small businesses can leverage AI tools like Microsoft 365 Copilot and ChatGPT to boost productivity, streamline operations, and enhance decision-making. It highlights the risks of adopting AI without proper planning, such as data privacy issues and compliance gaps, and emph...
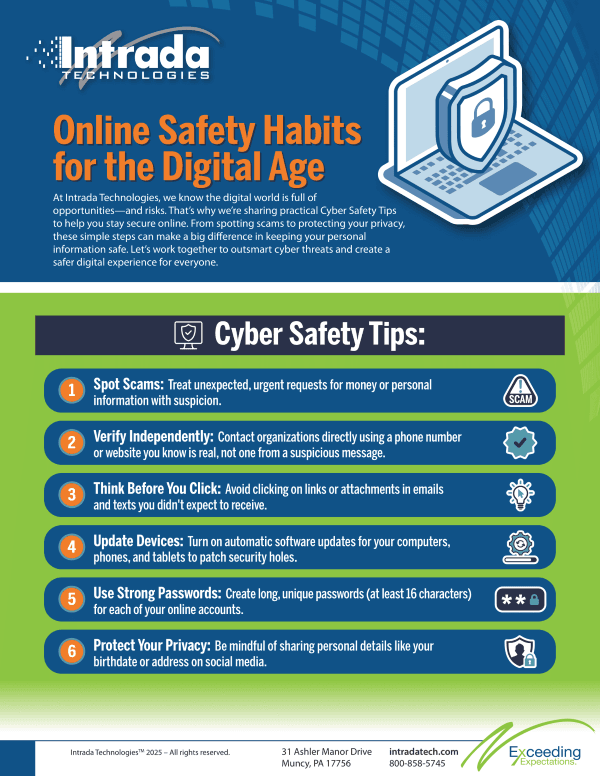
Online Safety Habits for the Digital Age

OVERVIEW
Navigating the digital world requires the same caution and awareness we use in everyday life. By adopting proactive habits like spotting scams, verifying suspicious requests independently, avoiding unexpected links, keeping devices updated, and using strong passwords, you can protect yourself from modern cyber threats. These simple yet effective practices empower you to stay secure and confident in an increasingly connected world.
INDEPTH

Navigating the online world has become a part of our daily lives, much like locking the front door or fastening a seatbelt. Just as we learned to check the safety seal on a food container, we can also adopt new habits to help keep us secure in today's digital environment. These practices are not about fear; they are about awareness and building confidence.
Thinking about online safety is like how we've always approached personal security. We learned to be cautious of strangers and to double-check things that seemed too good to be true. The same principles apply online, but the tools and methods have changed. This guide will take practical steps you can take to protect yourself from modern digital threats.
Spotting Modern Scams
Scams have evolved from in-person tricks to digital attempts that reach you via email, text, and phone. Criminals often try to create a sense of urgency, pressuring you to act quickly without thinking.
A common tactic is to demand payment via unusual methods such as gift cards, wire transfers, or cryptocurrency. A legitimate business or government agency will not ask for payment this way. It's helpful to treat any unexpected, urgent request for money or personal information with a healthy dose of suspicion, even if the message appears to come from a friend, family member, or a familiar company. If a demand feels strange, it’s likely a scam. It is perfectly acceptable to hang up the phone or delete the message.
The Importance of Independent Verification
In the past, if you received a questionable request, you might have called a neighbor or visited your bank in person to confirm it. Today, that same verification process is just as crucial, but it requires a different approach.
Cybercriminals have become skilled at impersonating others. They can spoof caller ID to make it look like they are calling from a trusted number, create convincing but fake websites, and even use
If you receive a suspicious email, text, or call, the best first step is to pause. Do not respond directly or use the contact information provided in the message. Instead, find the organization's official phone number or website yourself. For example, look up your bank's phone number on the back of your debit card or through a search engine and call them directly to verify the request.
Think Before You Click a Link
We used to toss junk mail into the trash without a second thought. The digital equivalent of junk mail—unsolicited emails, texts, and social media messages—requires a similar but more cautious approach.
Dangerous links can be hidden in these messages. Clicking on one could install malicious software (malware) on your device without you even knowing. This malware can steal your personal information, like passwords and banking details. A good rule of thumb is: if you didn’t expect it, don’t click it. This applies to attachments and even "unsubscribe" buttons in suspicious emails, which can sometimes be a trick to confirm your email address is active.
Keep Your Digital Locks Strong: Device Updates
If you lost a house key, you would likely change the locks to keep your home secure. Software updates for your computer, smartphone, and tablet serve a similar purpose in the digital world.
Developers regularly release updates that patch security holes and protect your devices from the latest known threats and viruses. Hackers are always looking for these vulnerabilities to exploit. By keeping your software up to date, you are installing the newest digital locks to keep them out. The easiest way to manage this is to turn on automatic updates whenever the option is available.
Create Stronger Passwords
Many of us remember when a simple four-digit PIN was all we needed for the ATM. Online accounts require much more robust protection. Criminals use powerful automated tools that can guess short, simple passwords in a matter of seconds.
A strong password is your first line of defense for an account. It should be long, unique, and complex. Aim for at least 16 characters and use a mix of uppercase and lowercase letters, numbers, and symbols. Most importantly, use a different password for each of your online accounts. This way, if one account is compromised, the rest of your digital life remains secure. Using a reputable password manager program can help you create and store these complex passwords safely, so you only must remember one master password.
Protect Your Personal Information Online
We've always known that some things are best kept private. That wisdom is more important than ever in the age of social media.
Sharing too much personal information online—like your full birthdate, home address, or details about your daily routine—can give criminals the pieces they need to commit identity theft or target you for scams. It's wise to review the privacy settings on your social media accounts and be mindful of what you share and with whom. Consider what someone could do with the information you post before you make it public.
Understanding Invisible Threats
One of the biggest challenges with cybercrime is that it is often invisible. A break-in or a stolen car is immediately apparent. The consequences of clicking a malicious link, however, may not be.
Malware can operate silently on your device for weeks or months, collecting your data without any outward signs of a problem. You might not realize you’ve been the victim of a scam until you notice strange charges on your credit card statement or find an account has been locked. This is why proactive online safety habits are so important. They form a digital security system that helps protect you from threats you cannot see.
You Have the Power to Stay Safe
Building strong online safety habits is an empowering step toward navigating the digital world with confidence. By understanding how threats have changed over time, you can apply simple, practical measures to protect yourself and your information.
AI and SEO: Reshaping the Future of Search
SEO is evolving with the rise of AI, transforming search engines into answer enginesthat prioritize direct, conversational responses. To stay visible, businesses must optimize their content for AI-driven algorithms, focusing on structured, authoritative, and user-intent-driven information. By levera...